Bit9 has released a report that outlines a host of fairly serious concerns around Android devices and app permissions. To be upfront: Android isn’t special in this regard, as if you have a Blackberry, iPhone, or Windows Phone Device you’ll also find a pile of apps that have very, very strange permission requests (e.g. can a wallpaper application access your GPS and contact book?). The video (above) is a quick overview of some findings; the executive summary can be found here and the full report here (.pdf).
Tag: Android
A great of speculation exists around mobile companies of all stripes: are they secure? Do they secretly insert backdoors for government? What kinds of assurances do customers and citizens have around the devices?
Recently these concerns exploded (again) following a Reuters article that notes serious problems in ZTE mobile phones. There are a series of reasons that security agencies can, and do, raise concerns about foreign built equipment (some related more to economics than good security practice). While it’s possible that ZTE’s vulnerabilities were part of a Chinese national-security initiative, it’s entirely likely (and more probable) that ZTE’s backdoor access into their mobiles is a genuine, gigantic, mistake. Let’s not forget that even ‘our’ companies are known for gross security incompetence.
In the ZTE case it doesn’t matter if the backdoor was deliberate or not. It doesn’t matter if the company patches the devices, either, because a large number of customers will never apply updates to their phones. This means that, for all intents and purposes, these devices will have well publicized security holes for the duration of their existence. It’s that kind of ongoing vulnerability – one that persists regardless of vendor ‘patches’ – that is increasingly dangerous in the mobile world, and a threat that is arguably more significant (at the moment) than whether we can trust company X or Y.
Casey Johnston, over at Ars Technica, has a two-pager complaining about how tech companies design and market so-called “Ladyphones.” It’s a quick read that picks up on earlier critiques about how certain colours, and reduced technical capabilities, are associated with derogatory gender perceptions.
That said, there are at least two elements of her piece that fall short to my mind: her analysis of the BlackBerry Pearl and of the LG Windows Phone.
Johnston argues that the BlackBerry Pearl was a device marketed for women, and emphasizes the device’s high costs and pink colouration in the UK as an example of trying to extract more money from a female demographic than would be extracted from a male demographic. She also cites the Pearl’s bizarre keyboard format and limited technical specifications to further reinforce her thesis that manufactures sell second-rate products to the female market.
As someone who owned an original Pearl 8100 I don’t know how fair her critique of RIM’s product is. Pearls were RIM’s attempt to get into the consumer market generally, with the position that a full-sized keyboard was intimidating and offsetting to male and female consumers alike. Moreover, the sizes of RIM’s other smartphones at the time – designed pre-iPhone, let’s not forget! – were offsetting to most regular, non-business, consumers.
The Pearl tried to find a balance between size, consumer market expectations, and traditional BlackBerry functionality. It was also comparatively cheaper than most other smartphones at the time (and, I would note, cheaper than the popular Motorola RAZER phones), though RIM and its carrier partners haven’t necessarily reduced the costs of the phone appropriately in all regional markets. Original colours lacked pink entirely: you could buy them in black or red. New colouring – and targeting – towards particular market segments is arguably more the result of an expanded smartphone market than anything else.
I would note than Johnston is far more generous towards RIM’s marketing and branding departments than, well, any other journalist that I’ve previously read. Her assumption that RIM was so forward thinking as to brand a consumer device ‘Pearl’ to target women is massively overestimating RIM’s (traditionally very, very, very, very poor) marketing and branding departments. Finally, the technical specs of RIM’s devices are criticized from all corners, regardless of the colour or class of device (i.e. Pearl, Curve, Torch, Bold, etc), and regardless of whether the device is targeted at professional, prosumer, or consumer markets.
The other issue with the article is her analysis of the LG Windows Phone. What she’s dead right on: LG ‘partnered’ with Jill Sander to inflate the device’s cost and try to make it appeal to a certain market segment. Yep, that’s attempting to sell a device to consumers interested in or intrigued by Sander’s line of products. Where Johnston is wrong, however, is in her effort to equate low-speced Windows Phones with high cost phones.
Unlike Android and iPhone, Microsoft’s mobile phones almost universally have poor technical specifications compared to the competition. That said, Microsoft has tweaked their devices such that the specifications really don’t matter: you get excellent performance in spite of the device using older tech. As such, I don’t really think that the technical critique rings terribly true – women aren’t expected to purchase crappy Windows phones any differently then men are – though I certainly agree around the ‘branding’ of the LG device to unnecessarily inflate costs and attract a dominantly female market.
Anyways: go read the piece and develop your own opinion. Despite my two bones to pick with her evidence I think that the thesis holds and is well supported. She’s created a piece that’s short and critical, if not as deep or as powerful a critique as I’d have liked. Hopefully we see more tech sites – and mainstream news sources! – similarly take companies to task for their attempts to sell second-rate, unnecessarily gendered, products to women.
What the Apps Can Access
![]()
Just a few of the mobile phone apps that hoover up your information when you run them on your Android device.
Papers on Android Mobile Malware
Android often receives high levels of criticism when hostile programs are found in its respective app stores. While anger is high, how prevalent is malware in Android markets? A series of papers, curated by Security Research Computer Laboratory at the University of Cambridge, examine just those questions. Go read them!
Watching the back-and-forth yesterday about the whole Microsoft Office for iPad thing was nothing if not amusing. The basic rundown:
“It’s coming, here it is.” “That’s not it.” “Yes it is.” “No it’s not, but we didn’t say it’s not coming.” “A Microsoft employee showed it to us.” “No…
MG has an interesting analysis on what Office for iPad might mean. I have to admit, if MS partners with Apple to bring real office software to the iPad then another sword will be levied at Google’s throat. I still – as a professional writer – despise using Google Docs for anything but the most minimal tasks: it just doesn’t meet my requirements for ‘real’ word processing.
The takeaway? Office would add to the ‘professional’ status of the iPad without taking away from the iPad’s ‘consumer friendly’ branding. This would further exacerbate the issues that Google’s tablets face while simultaneously challenging RIM’s own advertising that the PlayBook is ‘the’ tablet for professionals. It would definitely be a coup for both companies against their competitors, and so well worth watching for.
Symantec is warning that the next generation of smartphone viruses has come:
Researchers from security vendor Symantec Corp. have identified a new premium-rate SMS Android Trojan horse that modifies its code every time it gets downloaded in order to bypass antivirus detection.
This technique is known as server-side polymorphism and has already existed in the world of desktop malware for many years, but mobile malware creators have only now begun to adopt it.
A special mechanism that runs on the distribution server modifies certain parts of the Trojan in order to ensure that every malicious app that gets downloaded is unique. This is different from local polymorphism where the malware modifies its own code every time it gets executed.
This is a clever means to avoid the rudimentary analysis systems that the major vendors use to ID malware. It’s also (another) indication of how important antivirus is going to become for the mobile marketplaces. I suspect that, by the end of the year, a lot of users (on iOS, Android, and the rest) are going to wish that the post-Steve Jobs smartphones on the market today met Jobs’ initial thoughts regarding smartphones when Apple released the iPhone. Specifically, he held that:
He didn’t want outsiders to create applications for the iPhone that could mess it up, infect it with viruses, or pollute its integrity
While our pocket computers are better now that apps are available, I can’t help but think that Jobs’ earliest worries are now looming at today’s potential nightmares.
Symantec has identified 13 apps on the Android Market that are all hiding Android. Counterclank, a Trojan horse that steals information, and could also download more files and display ads on the device.
These apps are still available on the Android market, and up to five million handsets could be infected. The popularity in Android will continue to make it a lucrative target. Unless Google does more to prevent such apps appearing, it could mean the start of defection of users to other systems.
Click on above link for more.
For emphasis: up to five million handsets could be infected. That’s it, I’m calling it: Android is the new Windows for security and virus defence. Reminds me of the late 1990s and early 2000s for the number of reported actionable vulnerabilities being reported on an almost daily basis.
Useful Warnings

THIS is the kind of actionable, helpful, warning information that should be presented to end-users. It gives them the relevant information they need to choose ‘Cancel’ or ‘Add Anyway’ without scaring them one way or the other. If the jailbreak community can do this, then why the hell can’t the big players like Apple, RIM, Google, Microsoft and the rest?
Android & iPhone Update History
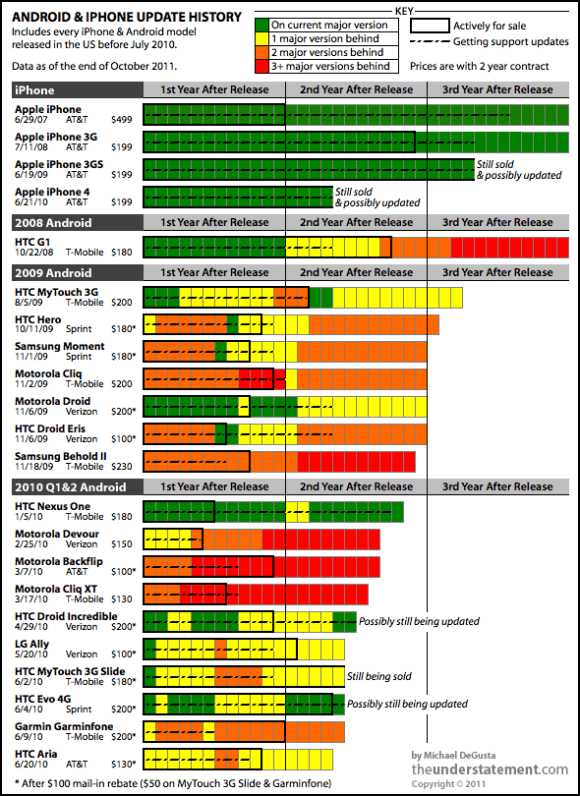
The seriousness of Android’s (lack of) security updates cannot be overstated. Phones that do not receive security updates can be subject to many of the most serious security attacks – such as man in the middle attacks, certificate-based MITM attacks, browser-based attacks, and so forth – and users remain ‘locked’ to their phones because of years-long contracts.
In essence, Android users on lengthy contracts with carriers are forcibly, contractually, linked to long-term security sinkholes.
This is an absolutely inexcusable situation, and one that Google, phone vendors, or carriers should be legislatively mandated to remedy.
