“Generally, things are not looking great with Google. I think that people have given Google a lot and with that they’ve trusted [Google] will do the right thing, that they will focus on the user and that their won’t be any surprises,” Marlinspike told IT Pro. “That’s turning out to not be true. They’re not really holding up their end of the bargain there.
“Now they’re saying you have until this time to change your mind, but it’s not about just opting in to providing data, it’s opting in in terms of connecting your life to a network that is controlled by Google.
“It’s difficult to now transition out of that. They were able to build that network through that trust and I feel like it’s not exactly fair for them to change the rules.”
~Moxie Marlinspike, January 26, 2012
Tag: Security
Android & iPhone Update History
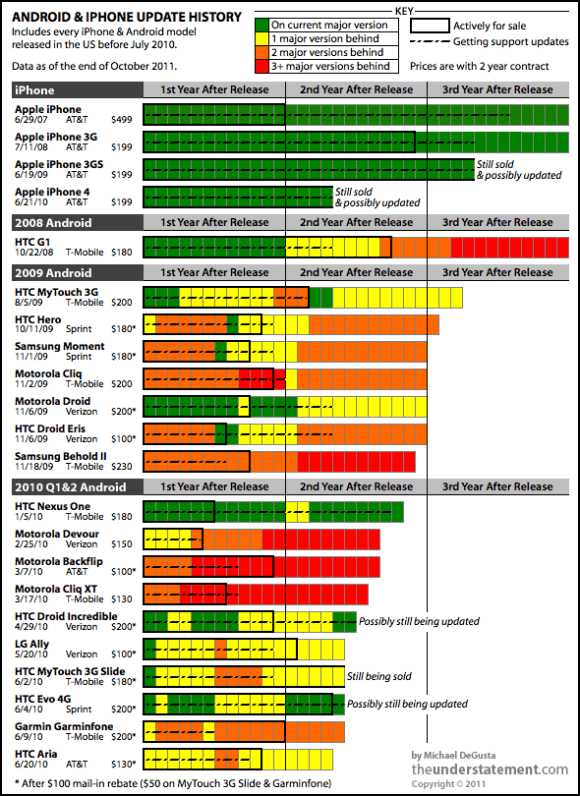
The seriousness of Android’s (lack of) security updates cannot be overstated. Phones that do not receive security updates can be subject to many of the most serious security attacks – such as man in the middle attacks, certificate-based MITM attacks, browser-based attacks, and so forth – and users remain ‘locked’ to their phones because of years-long contracts.
In essence, Android users on lengthy contracts with carriers are forcibly, contractually, linked to long-term security sinkholes.
This is an absolutely inexcusable situation, and one that Google, phone vendors, or carriers should be legislatively mandated to remedy.
…[Graham Thompson, president of Ottawa-based Intrinsec Security Technologies] cautions that RIM’s plans to tap into the Android marketplace could place a serious security burdern on the beleaguered company. An Android adherent himself, he nevertheless says the potential for breaches with Android apps threatens the core of RIM’s business strategy.
“I don’t understand why an [Android] application, for example, like a flashlight, requires Wi-Fi access or Internet access. It just makes no sense to me. Yet people are willing to say, ‘Yeah, go ahead. I don’t care about the privileges that this application is looking for. I just want my flashlight.’ And what impact does that have on corporate data is one of the main questions.”
I’m not exactly happy with the (impoverished) state of Android or iOS security. I’m happier (though I refrain from the full on “happy”) with RIM’s approach to data sharing with their app market (I’ve documented here some of the highly technical, and unwieldily, means that RIM notifies customers of security concerns). That said, I would wait before pronouncing that RIM’s integration of Android will lead to doom.
Specifically, those who have dealt with the RIM/Android integration have reported that Android apps do not get free reign on the device. This means that key Android ‘hooks’ are not always available, thus limiting the ‘damage’ they can do to a particular security profile.
Moreover, we cannot look at the integration without also considering the role of BlackBerry fusion, a system that intentionally hives off professional and personal ‘sections’ of the device. This segregation (in theory) should mean that even if an Android app breeches the RIM personal security protections, that the app should not have access to the professional side of the device and data contained in this element of the device.
Does this necessarily save the end-consumer, buying the device from Rogers, O2, or other wireless firm? No. Does it save businesses (a key market, and most zealous for, security assurance)? Much more likely.
More Playbook UI Fail
![]()
This is (another) security freak-out from the PlayBook. Is it really the case that Quantcast isn’t properly registering their certificates? What does it mean for the end-user to deny verifying the certificate?
The information contained in this screenshot lacks actual actionable information for most end-users, and they’re instead given a choice between X and Y without having any clear understanding of what either X (Decline) or Y (Accept) entrails.
Iran clamps down on internet use
From the Guardian a while back, we learn:
Iran is clamping down heavily on web users before parliamentary elections in March with draconian rules on cybercafes and preparations to launch a national internet.
Tests for a countrywide network aimed at substituting services run through the world wide web have been carried out by Iran’s ministry of information and communication technology, according to a newspaper report. The move has prompted fears among its online community that Iran intends to withdraw from the global internet.
The police this week imposed tighter regulations on internet cafes. Cafe owners have been given a two-week ultimatum to adopt rules requiring them to check the identity cards of their customers before providing services.
Since the Green Revolution the Iranian government has massively committed resources to identifying and undermining Iranian citizens’ ability to communicate with one another using electronic systems. From their integration of deep packet inspection into their main ISP networks – and configuring them to identify and stop some kinds of encrypted traffic – to the creation of cyber-police, and now attempts to physically identify those who use public computers, it is getting harder and more dangerous for Iranians to communicate with one another over the Internet.
You should go read Chris’ paper, available at SSRN. Abstract below:
Today, when consumers evaluate potential telecommunications, Internet service or application providers – they are likely to consider several differentiating factors: The cost of service, the features offered as well as the providers’ reputation for network quality and customer service. The firms’ divergent approaches to privacy, and in particular, their policies regarding law enforcement and intelligence agencies’ access to their customers’ private data are not considered by consumers during the purchasing process – perhaps because it is practically impossible for anyone to discover this information.
A naïve reader might simply assume that the law gives companies very little wiggle room – when they are required to provide data, they must do so. This is true. However, companies have a huge amount of flexibility in the way they design their networks, in the amount of data they retain by default, the exigent circumstances in which they share data without a court order, and the degree to which they fight unreasonable requests. As such, there are substantial differences in the privacy practices of the major players in the telecommunications and Internet applications market: Some firms retain identifying data for years, while others retain no data at all; some voluntarily provide government agencies access to user data – one carrier even argued in court that its 1st amendment free speech rights guarantee it the right to do so, while other companies refuse to voluntarily disclose data without a court order; some companies charge government agencies when they request user data, while others disclose it for free. As such, a consumer’s decision to use a particular carrier or provider can significantly impact their privacy, and in some cases, their freedom.
Many companies profess their commitment to protecting their customers’ privacy, with some even arguing that they compete on their respective privacy practices. However, none seem to be willing to disclose, let alone compete on the extent to which they assist or resist government agencies’ surveillance activities. Because information about each firm’s practices is not publicly known, consumers cannot vote with their dollars, and pick service providers that best protect their privacy.
In this article, I focus on this lack of information and on the policy changes necessary to create market pressure for companies to put their customers’ privacy first. I outline the numerous ways in which companies currently assist the government, often going out of their way to provide easy access to their customers’ private communications and documents. I also highlight several ways in which some companies have opted to protect user privacy, and the specific product design decisions that firms can make that either protect their customers’ private data by default, or make it trivial for the government to engage in large scale surveillance. Finally, I make specific policy recommendations that, if implemented, will lead to the public disclosure of these privacy differences between companies, and hopefully, create further market incentives for firms to embrace privacy by design.
From the article:
If someone steals your card, they won’t be able to use it without your code unlocking the number and coding the strip. Since the credit card number is generated fresh for each transaction, there is no data to be stolen in the case of a hack. Citibank is now using the cards in small pilot programs, and the company is hoping to see more banks and cities using the technology.
The dynamic nature of the magnetic strip opens up a number of other applications. I saw a card that had two numbers, so you can keep your business and personal accounts on the same card. You hit a flat button next to each number to select it; a light shines showing you which account is active, and the magnetic strip is coded with that number. Change accounts, and the magnetic strip is instantly reprogrammed. Each card comes with a battery that should last three years.
Of course, this technology is being developed because the US has been so bloody slow adopting the Chip + PIN system that most other nations are adopting. While there are certainly problems with Chip + PIN it makes a lot more sense to work on, and try to resolve, those problems instead of inventing convoluted new technologies to address known-bad systems. Curious about the payment card fiascos? Check out the comments of the Ars article, you might learn a lot.
![]()
liberty+justice+equality+freedom = SECURITY !
This is what ‘balancing’ security with civil liberties often looks like in practice.
It’s code is available to third-parties, so we can check for intentional flaws in the enhancements that the NSA has integrated into the Android OS. Still not sure how comfortable I’d be using an OS designed by the folks that do a considerable amount of US SIGINT and COMINT.
Jon Evans, over at TechCrunch:
More than two-thirds of iOS users had upgraded to iOS 5 a mere three months after its release. Anyone out there think that Ice Cream Sandwich will crack the 20% mark on Google’s platform pie chart by March? How about 10%? Anyone? Anyone? Bueller?
OS fragmentation is the single greatest problem Android faces, and it’s only going to get worse. Android’s massive success over the last year mean that there are now tens if not hundreds of millions of users whose handset manufacturers and carriers may or may not allow them to upgrade their OS someday; and the larger that number grows, the more loath app developers will become to turn their back on them. That unwillingness to use new features means Android apps will fall further and further behind their iOS equivalents, unless Google manages – via carrot stick, or both – to coerce Android carriers and manufacturers to prioritize OS upgrades.
Android fragmentation is a pain for developers and, perhaps even more worryingly, a danger for users who may not receive timely security updates. To be sure, Apple rules-the-roost when it comes to having better updated device, insofar as users tend to get their updates when they become available. Whether those updates contain needed security upgrades is another matter, of course, but Apple at least has the opportunity to improve security across their ecosystem.
Unfortunately, where Apple sees their customers as the people using the devices, Google (and RIM) both have mixed understandings of who are their customers. Google is trapped between handset manufacturers and carriers whereas RIM is largely paired with the carriers alone. Neither of these companies has a timely, direct, relationship with their end-users (save for RIM and their PlayBook, which has routine updates that bypass their mobile devices’ carrier-restrictions) and this ultimately ends up hurting those who own either companies’ mobile devices.